Intro
The Cyber Security Challenge is a yearly online event where students from all around the country come together to solve cyber security related challenges. People compete in teams on a platform full of challenges, where each solved challenge awards a certain amount of points. The more a challenge is solved, the less it's worth, so knocking out challenges earlier than the others is a big factor of how highly your team will rank. Some challenges are also easier than the others, but that does means they quickly lose their value. Only the top few teams with the most experience and challenges solved qualify to go to the final on a later date, where the ultimate winners are crowned.
Solving challenges
This year was the second time I participated in the event. Due to being busy, I didn't have as much time for it as previous year, so I had to resort to a regime of checking in every so often when I had the time to give a crack at solving some challenges. Our team was relatively laid back as well and since we generally weren't available to participate in the final later either, so we didn't have to worry about scoring well. That didn't mean we couldn't give it our best shot, however! I ended up working on a couple of different challenges, and I would like to expand upon two of them in this post.
Pirates Treasure
A teammate of mine started a challenge where he needed to decode an image of Captain Hook. At first, it seemed there wasn't anything peculiar going on. Just an image of your favourite childhood captain. Or maybe yours was Piet Piraat? I digress. Anyways, it's just a regular image like any other with no visual hints or oddities in sight.

...until you analyse it. As it turns out, files were hidden in the binary data of the image, which can be extracted using the command binwalk -e captainhook.png. When doing so, another image is produced, as well as a text file:
You're sharper than this bloody Peter Pan ! But the treasure be still hidden deep mate ! Aye, the X marks the spot, but the island is full of crocodiles ready to devour you.
Only under the moonlight does the true path reveal itself.
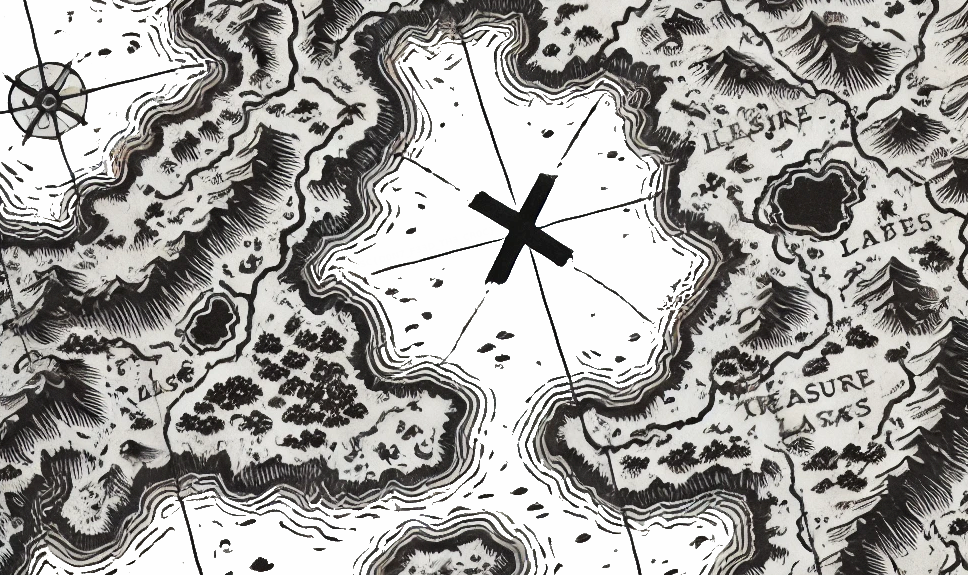
This is where my team mate was stumped. What was the next step? I joined in to help and tried all sorts of things to figure it out: analyzing the text for its use of capital letters or trying binwalk and other steganographic decoding tools on the new image, but with no luck. It was only after I read the text again with full concentration that I got the hints.
The "x marks the spot" gives you direction on where to look on the image and the "Under the moonlight does the true path reveal itself" refers to the idea that the lighting conditions weren't quite right just yet to see the solution. I opened the image in Krita and upped the contrast. There it was. Faintly written next to the X. The final flag marking the challenge solved.
.png)
%20-%20zoom%20in.png)
When you hand in this piece of text on the CTF platform, you show that you've figured out the challenge and your team gets awarded the points. These pieces of text, called flags, are often wrapped in the structure CSC{...}, so you know when you've found the answer. Not all challenges have them and sometimes you are expected to hand in another solution, but this one did, clearly communicating the end of the exercise.
Our encryption is secret
In another challenge, I was presented with a zip file containing 19 of other zip files. I could extract the outer zip file with no problems, but upon trying to open the contained ones I was time and time again prompted to supply a password. Since I didn't have any, I looked at the challenge description for clues. It read as follows:
Me and my best friend communicate exclusively via password-protected ZIP files. It's a great way to ensure our privacy, and on top of that, it's extremely portable. It does, however, tend to wear down our numpads.
The first part is definitely fluff and is there to shape context for an otherwise seemingly random challenge. But the last part is the important bit: why would they specifically wear down their numpads when entering the password? It must have something to do with numbers. Maybe the author is trying to communicate that all passwords are numeric in nature...
I looked online for a tool that could help me crack the files and found this GitHub repository. By writing a short script that loops over all zip files and runs the cracking tool on each one, I could rapidly try a bunch of password number combinations one after the other. And it worked! After a few seconds I could see that the passwords for the first few files were already cracked. Hooray! I checked if the passwords worked and they did.
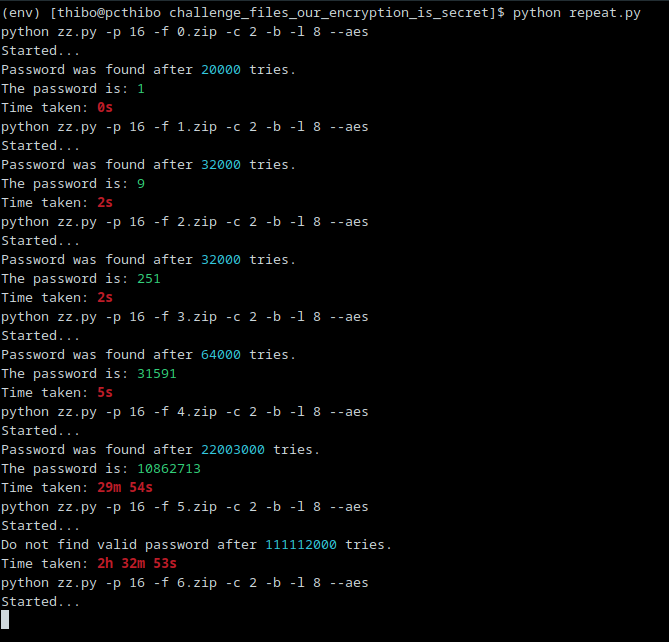
Each opened zip file gave me a text document containing a single character. When I concatenated all the characters of each file, I got the start of a flag (CSC{O), so it was clear to me that I needed to know basically all passwords to all the zip files before I could hand in a full flag and show that I've solved the challenge.
But as you may see, the joy of finding the first few passwords quickly faded. It took forever to find the password for the fifth file. Half an hour in fact. I let it run for a few more hours in the background, but it couldn't find the sixth password after giving up 2 and a half hours in. It was very clear that any further attempt to bruteforce another file was going to be in vain. We were on a clear exponential curve. I could probably modify the parameters of the tool so it wouldn't give up that quickly, but I can't wait for more than four hours for the next character. And what about the one after that? The event would be long over by the time I've got the entire flag!
No worries though, all challenges are solvable and there must be another way. I lined up all the passwords I had: 1, 9, 251, 31591, 10862713. Maybe this could be a mathematical sequence? I checked OEIS, the Online Encyclopedia of Integer Sequences, and found A075987, starting with the exact numbers I already had. I tried the next few integers on the site as passwords to my ZIP files and they all worked. I knew I was getting close to solving the entire thing.
They didn't make it easy though. OEIS doesn't provide enough numbers for this sequence to crack all files, so I rapidly cooked up a Python script that took the accompanying mathematical formula and produced the remaining numbers. This way, I was able to produce the passwords for all of the zip files:
primes = [2, 3, 5, 7, 11, 13, 17, 19, 23, 29, 31, 37, 41, 43, 47, 53, 59, 61, 67, 71, 73, 79, 83, 89, 97]
def gen_oeis(n): # https://oeis.org/A075987
values = [1]
for i in range(n):
p_acc = 1
for j in range(i):
p_acc *= primes[j]
values.append(values[len(values)-1]*primes[i]**3+(p_acc)**3)
return values
print(gen_oeis(19))
I concatenated all the characters contained within the text files of each zip and produced the full flag, which marked the finish of the challenge: CSC{OEIS_5eq5_rUl3}.
Our encryption is secret was the only significant problem I solved all by myself this year. Last year I had loads more, but the challenges were seemingly harder this time around and I couldn't bring any others to completion. I am still grateful I've solved a single one though 🙂
Conclusion
Our team ended up ranking 141 out of 308, which isn't so bad given the circumstances. I'm a bit disheartend that I couldn't solve more, but I'm glad I could still contribute to the pile of points by solving one myself and helping the others with solving their challenges. The competition is fierce for a reason and I am happy to see the amount of enthousiasm in the cyber security sphere. I've always loved the field, even though I am still a software engineering student afterall.
